Let It SNOW
Using ServiceNow to send malicious links
ATTACK
9/17/20252 min read


2025 seems to be the year of abusing ServiceNow (SNOW) for Red Team operations. Earlier this year, MDSec wrote a tremendous post about using ServiceNow during Red Team engagements which can be found here: Red Teaming with ServiceNow. Additionally, while at RVASEC this Summer I was able to sit in on a great chat by Rotas Security about ServiceNow which can be watched here: Attacking and Defending ServiceNow. Shoutout to those two resources for inspiring us to dig into SNOW some more.
When attempting to replicate some of these attacks, I realized that many of them require a compromised user with high-level administrative privileges. But what can you do with a user account that has low privileges?
This is not an ground-breaking discovery and won't headline a DEFCON talk. I would not classify this as initial access but more of a post-compromise or internal threat social engineering attack vector. Enough with the small talk - when poking around SNOW I noticed that in the upper-right hand corner there was an icon for what appeared to be a chat feature.
When you click on the icon you are presented with the option to start a new conversation. Clicking that, I was presented with an option to choose a recipient.
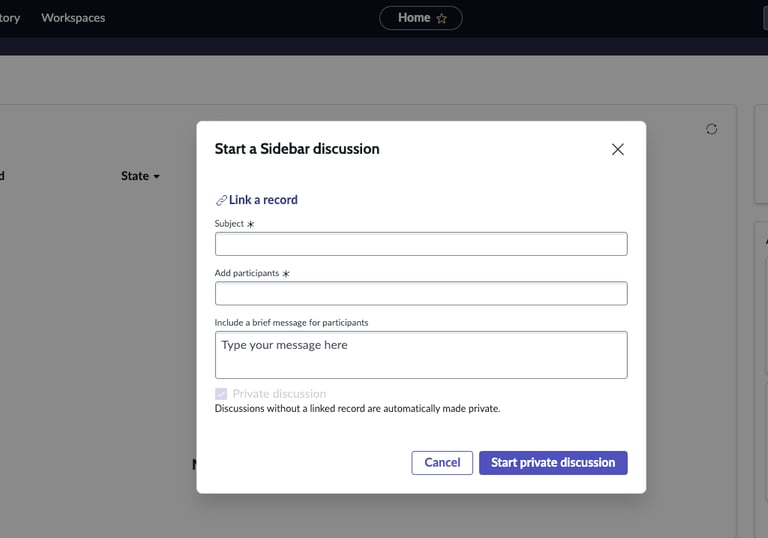
Now this is where it gets exciting because "Add participants" allows you to send to anyone within the domain the SNOW instances sits in.
I created a conversation with a team member and first sent a link as a plain IP address that was hosting a simple Python server. However, I couldn't really get any data that way so I configured a domain really quick and set up my Golang phishing infra that was described in previous post.
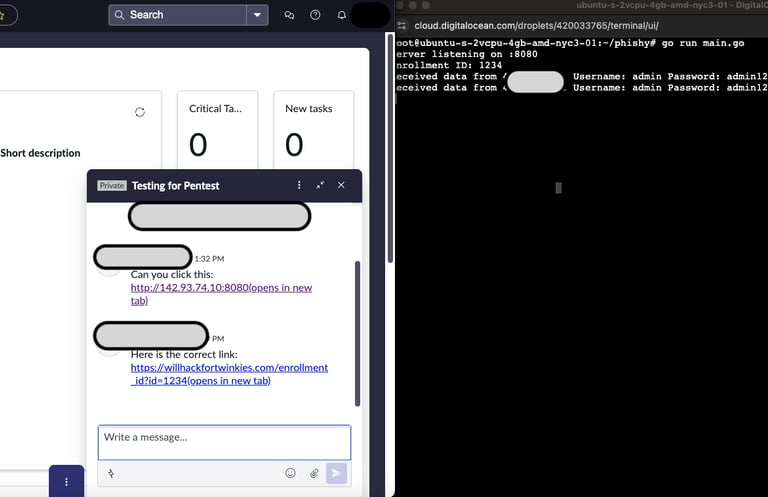

You might be thinking, "Big deal - you sent a link in chat why write a blog post about it?" Well, because this appears to be another example of living off trusted sites (LOTS). The Enrollment ID in the terminal shows only one click from the user which means the link does not get "clicked" by anything for inspection. Had this link gone through Outlook there would be two clicks present in the terminal but not with SNOW. You might also be thinking, "Yea but this was a SNOW lab so of course nothing was going to click it." Nope. This test was conducted in an enterprise SNOW instance where your usual stack of EDR and AV are present.
In conclusion, an insider threat or a compromised account can utilize this feature to attempt to socially engineer users with high privileges and broaden the attack surface.