MS Defender Phishing
Get full use out of your Microsoft license by running in-house phishing campaigns.
ATTACK
12/30/20243 min read


NOTE: This post is not applicable to everyone as it requires being within a company or having access to certain Microsoft licenses. So, why write it then? Because it involves phishing, and this is a phishing blog.
If you're new to a security role with aspirations of breaking into offensive security, and your company has a robust Microsoft license lining BG's pockets, here’s an idea for a productive side project: propose running an internal phishing campaign using Microsoft Defender. This approach eliminates the need for maturing a domain, crafting custom HTML, or bypassing Safe Links.
When presenting this idea, be sure to outline clear objectives and obtain proper permission. Of course, if you're just testing by sending to yourself to understand how it works, you know what they say: "It's easier to ask for forgiveness than permission."
Microsoft Defender Attack Simulation Training is only included in certain licenses and requires specific security roles to access. More information can be found here: Attack Simulation Training
After activating your Entra role, navigate to https://security.microsoft.com
From the main screen, click into the side panel and navigate to "Email & Collaboration" > "Attack simulation training"
Once you click into "Attack simulation training" there should be an option to "Launch a simulation."
Your first selection will be deciding how your phish will be delivered: Email or Teams. For the sake of this post, we will be walking through the email option.
After selecting email for your delivery, you will be given a wide range of specific campaigns to run.
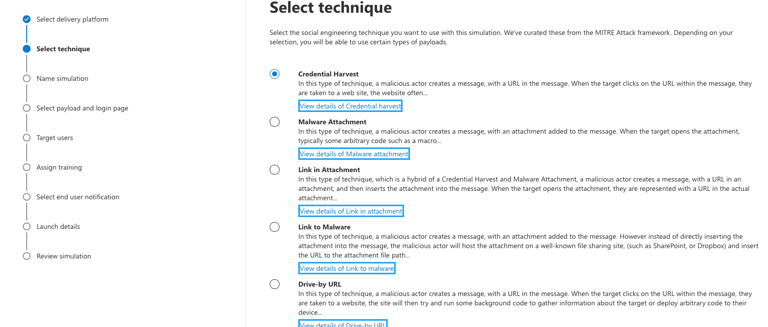
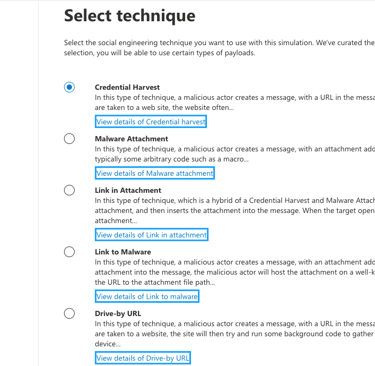
As you can see, there are several fun options to run. However, because this is your first rodeo and you're wanting to make a good impression we will keep it simple and roll with the "Credential Harvest" option.
Next, you need to name your campaign. My thought process for naming a campaign is if its a test run I will name it "PhishAreFriendsTesting". However, if it is a legitimate campaign and I need to easily access the metrics then I would name it something easy to pick out like "PhishAreFriends Q1 2025."
Still with me? Hope so. The fun part is coming up.
Now we have payload selection. You will have two options: Global or Tenant. Global payloads are emails and landing pages made by Microsoft and come with Defender. Tenant payloads are custom made by you or another internal employee. Again, this is the first campaign so we will use a Global payload.
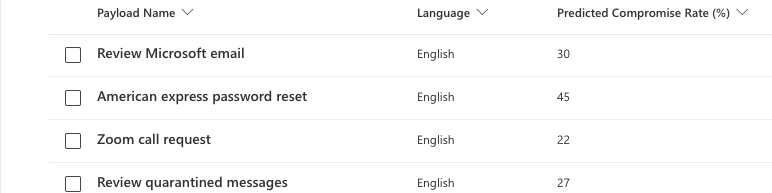
The Global payloads vary from Netflix lockouts to traditional Microsoft email notices. Additionally, you can click into each payload and view the details of it such as the email, the login page, and other information.
Once you have the payload set, next you select the users to send it to. Only send to users you obtained permission to send to. If your manager said, "Sure you can send some phishing emails to finance." Then only send emails to finance.
After you have selected the users, now you decide what happens if they click the link and enter their credentials.
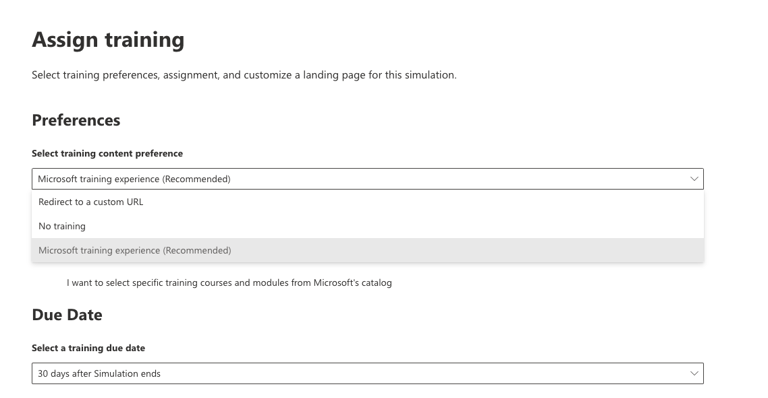
Your selection here ties back to what was discussed in your objective talks with the powers at be. If they are just wanting to know metrics then training might not be required. However, if they are wanting to increase user awareness then they may ask that those who fell for it to take the training. I recommend to decide this bit with management.
After the end user's fate is decided it is just a matter of scheduling the launch. Timing a phishing campaign can be a bit of an art, but in general ask yourself the question "When will a person be likely to see something at the top of their inbox and act on it?" Friday afternoon at 3pm? Probably not. Wednesday morning at 9am? Could be on to something.
Once your launch details are in place, you are good to review and submit. There you have it! You just saved your company big bucks by running a phishing campaign in house with a tool that is already in place.