SPF 50
Don't forget your sunscreen! Along with DMARC, DKIM, and all the other things.
ATTACK
10/30/20242 min read


An email contains more than just a sender, recipient, subject line, and body. In fact, a secure email requires three main components:
SPF
DKIM
DMARC
Getting a phishing email to land in an inbox will require those three things to be present - but what are they?Here is a breakdown of each element:
SPF (Sender Policy Framework)
SPF is an email authentication protocol that helps prevent DNS from being spoofed by malicious actors. Establishing SPF in DNS essentially gives specific servers permission to send email from a specific domain. If the SPF does not pass, it will not be received by the inbox and rejected.
DKIM (DomainKeys Identified Mail)
DKIM is another authentication method to ensure that an email came from an authorized sender and was not tampered with during transit. Here is an example of what a DKIM record would look like in Cloudfare:
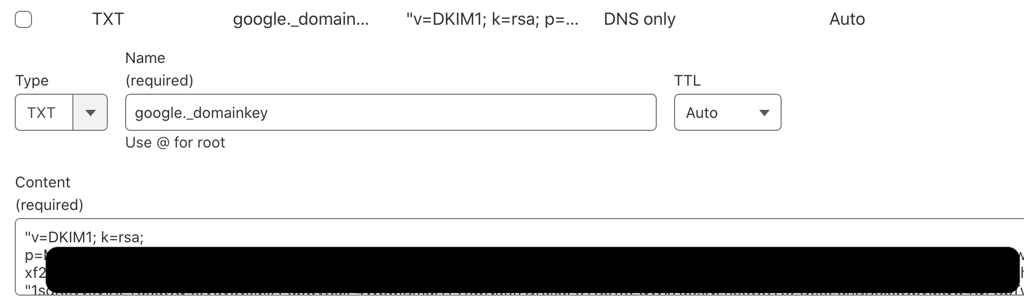
The DKIM key that is blacked out is also located in the Google Admin Workspace where the email address is managed. Google and Cloudfare use this connection to verify that the emails being sent from the listed domain is allowed.
DMARC (Domain-based Message Authentication, Reporting, and Conformance)
DMARC relies heavily on SPF and DKIM. DMARC mostly determines what happens to an email if SPF and DKIM fail. Here is a simplified flow chart of what could happen to an email once it hits DMARC if SPF and DKIM fail.
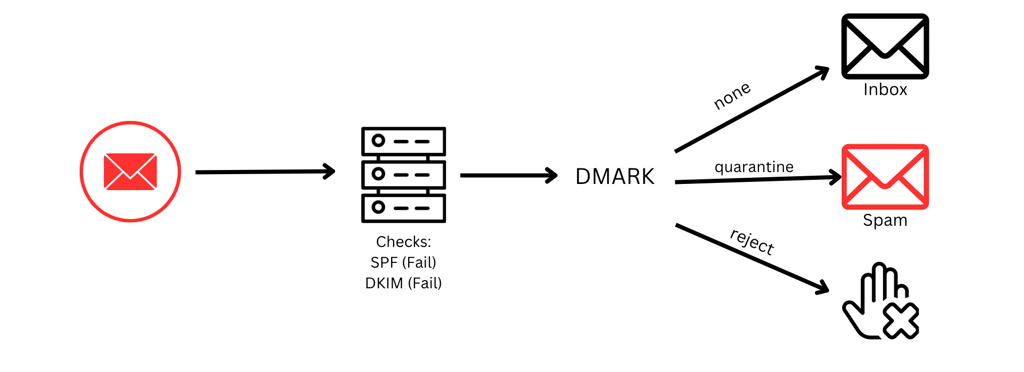
When setting up a phishing campaign, it is important to ensure that the proper DNS records are in place to help ensure your email lands. Otherwise, your emails will get burned and never see the light of the inbox.