Bad Case of the Mondays
From SaaS to watering hole attacks
ATTACK
11/13/20252 min read


In our last post, we discussed utilizing the messaging feature in ServiceNow to send malicious links and introduced the concept of LOTS. Looking for additional trusted sites to abuse, we took aim at monday.com.
Monday is a project management and productivity SaaS tool. Monday is also a great way of getting into Outlook, directing users to links and attachments, and double as a watering hole attack.


Watering hole attacks are just as they sound. As Splunk describes, "hackers target online platforms or websites that are frequently browsed by their target victims." Think websites such as online forums, collaboration sites, etc. Or in our case - monday.com
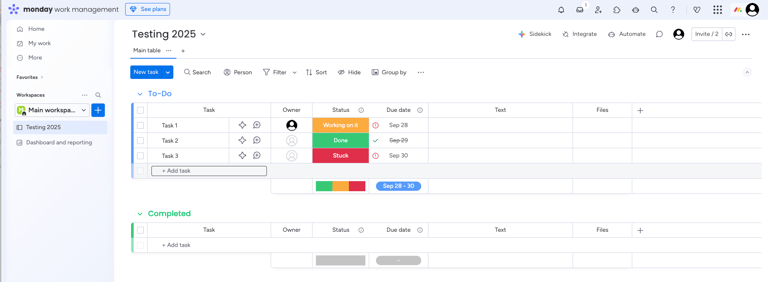
Using a GMAIL account, we were able to sign up for a free trial version of Monday to test with. Here we created our Workspace, "Testing 2025" - original we know.
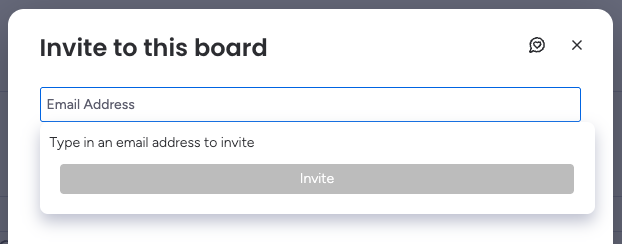
Navigating to the "Invite" button you are presented with the option to share the workspace with any email you enter. For testing, we sent it to an Outlook account.
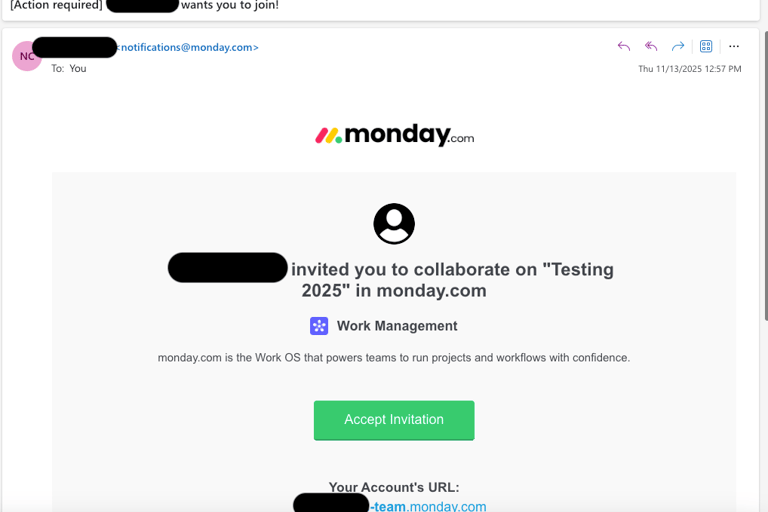
There you have it. The email comes in from the monday.com domain and the account URL is linked to monday.com. This eliminates the need to warm up an email address or age a domain.
Returning to our Workspace home screen we can highlight the watering hole vectors. On the Workspace home screen you are able to add columns to the Task lines. Two columns of interest for us are:
Text
Files
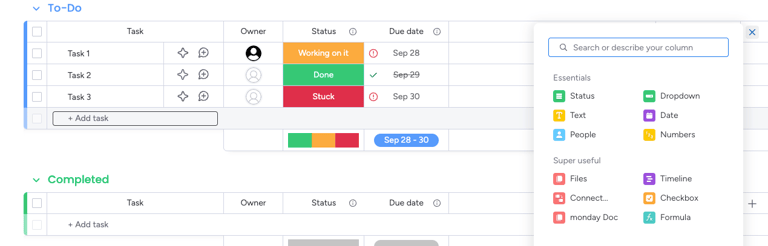
Within Text columns you can enter links for your watering hole victim to navigate to. Could be useful for directing them to a credential harvesting endpoint.
AND/OR!!
The File column allows for file upload. For testing, we were able to upload a Microsoft Word document and PDF. Both formats were accepted by Monday. The nice part? Once uploaded, the end user can download these files.
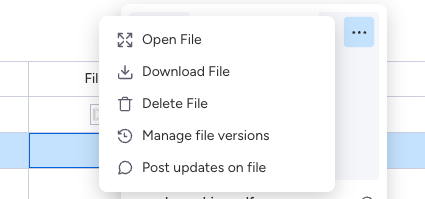
Although this vector would likely only have success with clients using Monday, it is still a great demonstration of how SaaS can be abused to for unintended purposes.